In the rapidly evolving digital world, adhering to website security best practices is of utmost importance. Cybersecurity threats like data breaches, DoS attacks, and ransomware have become more complex and frequent. Keeping your website secure is important for protecting data. It also helps maintain your reputation and build user trust.
This guide explores important parts of website security. It covers common threats and the weaknesses of open-source CMS. It also explains how to implement effective security measures and create a strong recovery plan.
To make your website safer, follow these security best practices. This will help create a more reliable online experience for your users in 2024.
Table of Contents
What does website security mean?
Website security is the practices and measures designed to protect your site from online threats and unauthorized access. It involves using different type of strategies that safeguard a website’s integrity, confidentiality, and availability to your users.
The primary goal of website security is to prevent cyber attacks, data breaches, and other malicious activities that could compromise your website’s functionality and reputation. As websites have evolved from simple HTML pages to complex environments with integrated development frameworks, the potential for cyber threats has significantly increased.
With over 2,200 cyber attacks happening each day, it’s vital to implement website security best practices. This includes measures such as encryption, access controls, regular updates, and continuous monitoring and audits to ensure ongoing protection against evolving threats. By doing so, you can mitigate risks and protect both your site and its users from harm.
Why is it important to secure your website?

Image by rawpixel.com on Freepik
Having a secure website is crucial for several reasons. Firstly, it protects sensitive data from cyber threats. Websites often collect and store personal information such as names, addresses, and payment details. Ensuring this data is secure is essential to prevent breaches that can lead to identity theft and financial loss. A secure website safeguards business and customer data from various types of web-based attacks, maintaining trust and confidentiality.
Secondly, website security is vital for maintaining your website’s functionality and uptime. Cyber attacks, such as Distributed Denial of Service (DDoS) attacks, can make a website unavailable to users, damaging your reputation and causing potential revenue loss. Protective technologies helps prevent such disruptions, ensuring that your website remains accessible and operational.
Additionally, compliance with data protection regulations is another critical reason for securing your website. Regulations like the General Data Protection Regulation (GDPR) mandate strict data protection practices. Non-compliance can result in hefty fines and legal repercussions. Ensuring your website is secure helps you stay compliant with these laws, as emphasized by Hagadone Technologies.
Overall, investing in website security not only protects your data and maintains functionality but also builds trust with your users and ensures compliance with legal requirements, ultimately contributing to the long-term success of your online presence.
6 Common website security threats

images by storyset on Freepik, gstudioimagen on Freepik, and macrovector on Freepik
Website security threats are more prevalent than ever, and understanding these threats is crucial for safeguarding your online presence. Here, we explore some of the most common website security threats and how they can impact your website.
Data breach
A data breach occurs when unauthorized individuals gain access to confidential data. This can result from vulnerabilities in your website’s security infrastructure, allowing hackers to steal sensitive information such as personal data, financial records, and login credentials.
Data breaches can lead to significant financial losses, legal repercussions, and damage to your brand’s reputation. Data breaches in 2024 have affected millions of individuals and organizations, underscoring the need for robust security measures
Denial of Service (DoS) and loss of website availability
Denial of Service (DoS) attacks aim to make a website unavailable by overwhelming it with a flood of traffic. This can result in significant downtime, loss of revenue, and a damaged reputation. Ensuring that your website remains accessible involves implementing measures such as traffic filtering, rate limiting, and employing a Content Delivery Network (CDN) to distribute traffic.
Ransomware
Ransomware attacks involve malicious software that encrypts your website’s data, rendering it inaccessible until a ransom is paid. These attacks can cripple business operations and lead to substantial financial losses. Regular backups and having a robust incident response plan are essential strategies to mitigate the impact of ransomware.
Cross-site scripting (XSS)
Cross-site scripting (XSS) attacks exploit vulnerabilities in web applications to inject malicious scripts into webpages viewed by users. This can lead to unauthorized access, data theft, and the compromise of user accounts. Implementing input validation and escaping untrusted data are key practices to prevent XSS attacks.
SQL and code injections
SQL and code injections occur when malicious code is inserted into your website’s input fields, exploiting vulnerabilities in the web application. This can lead to unauthorized access to your database, allowing hackers to manipulate, steal, or delete data. SQL injection attacks can severely disrupt website functionality and compromise sensitive information.
Stolen passwords
Stolen passwords can occur through phishing attacks, keyloggers, or database breaches. Hackers use stolen passwords to gain unauthorized access to user accounts and administrative areas of your website. Strong, unique passwords and multi-factor authentication are essential to prevent this type of attack.
How to tell if a site is NOT safe
While browsing, it’s crucial to recognize the signs of an unsafe website to protect yourself from potential cyber threats. Unsafe websites can lead to data breaches, malware infections, and other cyber attacks. Below, we outline some key indicators that a website may not be safe.
Missing the “S” in the HTTPS
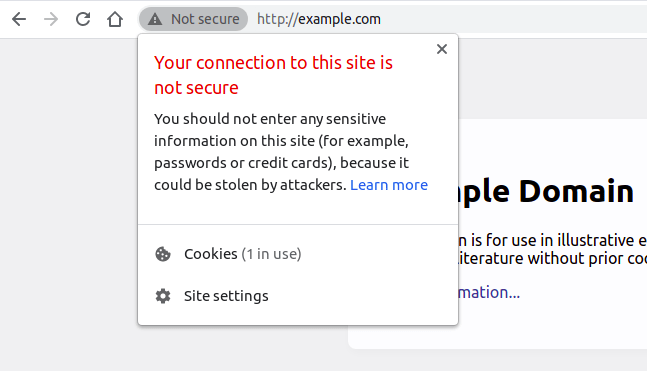
A secure website will typically use HTTPS (Hypertext Transfer Protocol Secure) rather than HTTP. The “S” in HTTPS stands for secure, indicating that the site uses encryption to protect the data exchanged between the user and the website. If a website only uses HTTP, it means the data is not encrypted and could be intercepted by malicious parties.
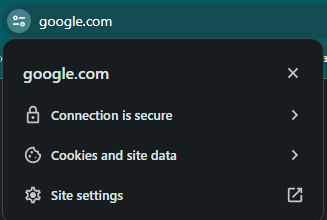
Always look for the padlock or the new security icon in the browser’s address bar as a sign of a secure connection.
Suspicious pop-ups

Frequent and unexpected pop-ups can be a red flag for an unsafe website. These pop-ups often contain malicious content or lead to phishing sites that attempt to steal your personal information. Reputable websites generally limit the use of pop-ups, and any that do appear should be directly related to the site’s content.
Malicious redirects
Malicious redirects occur when clicking a link or button on a website sends you to a different, often harmful, site. These redirects can lead to phishing pages or sites that automatically download malware. If you encounter unexpected redirects, it’s best to leave the site immediately.
Security warnings in your browser
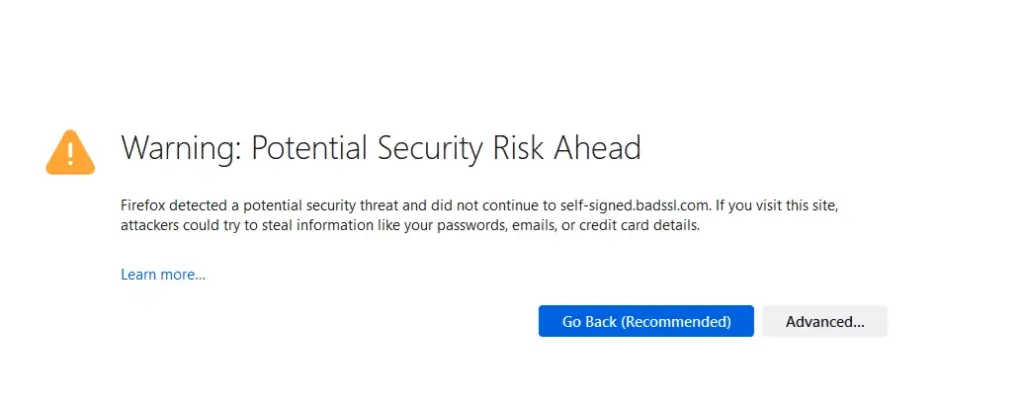
Modern browsers, such as Chrome, Firefox, and Edge, have built-in security features that warn users if a website is potentially unsafe. These warnings can range from alerts about expired SSL certificates to notifications about malware or phishing threats detected on the site. If you encounter a security warning in your browser, it is a clear indicator that the site might pose a risk to your personal information and overall security.
Search engine warnings
Search engines like Google and Bing also play a crucial role in keeping users safe online. If a website is compromised or hosts malicious content, search engines may display warnings directly in the search results. For example, Google might label a site with “This site may be hacked” or “This site may harm your computer.” Such warnings are red flags that the site is not secure and should be avoided until the issues are resolved.
Vulnerability databases
Vulnerability databases, such as the National Vulnerability Database (NVD) or CVE Details, track known security vulnerabilities in websites, applications, and systems. If a site you’re visiting is listed in these databases for known vulnerabilities that haven’t been patched, it’s a strong indication that the site is not secure. Regularly consulting these databases can help identify sites that might pose security risks.
Lacking a privacy policy
A legitimate and secure website will have a clear, accessible privacy policy detailing how user data is collected, used, and protected. If a site lacks a privacy policy, it could be a sign that it doesn’t adhere to standard data protection practices, which could put your personal information at risk. Always check for a privacy policy to ensure the site follows website security best practices for data.
Missing contact information
Secure and trustworthy websites will provide clear contact information, including an address, phone number, and email. If a site is missing this information or only offers a generic contact form, it may be a sign of a fraudulent or untrustworthy site. Transparent contact details are essential for user trust and accountability.
Bad copy and design
Image by Martin Luenendonk at FOUNDERJAR
Websites that have poor design, numerous typographical errors, and low-quality content often indicate a lack of professionalism and attention to detail. These sites may not invest in proper security measures, making them more vulnerable to cyber threats. A well-designed site with polished content is usually more reliable and secure.
Inaccurate WHOIS
WHOIS data provides information about the ownership and registration details of a domain. If the WHOIS information is hidden or falsified, it can be a sign that the site owners are trying to remain anonymous, which might indicate malicious intent. Accurate and transparent WHOIS data helps verify the legitimacy of a website and its operators.
Why hackers LOVE open source CMS

The reason that hackers are particularly drawn to open-source Content Management Systems (CMS) like WordPress, Joomla, and Drupal is due to their widespread use and open nature. These systems are incredibly popular because they offer flexibility, extensive community support, and numerous plugins and themes to enhance functionality. However, this popularity also makes them prime targets for cybercriminals.
One of the main reasons hackers love open-source CMS platforms is the accessibility of their source code. Since the code is open to everyone, it allows security researchers and developers to identify and fix vulnerabilities, but it also provides malicious hackers with the same opportunity to find and exploit weaknesses. The large user base of these CMS platforms means that a single vulnerability can potentially be exploited across thousands of websites, making them an attractive target for mass attacks.
Moreover, the extensive use of third-party plugins and themes in open-source CMSs adds another layer of risk. While these add-ons can significantly enhance website functionality, they are often developed by independent contributors who may not follow stringent security practices. As a result, plugins can introduce vulnerabilities that hackers can exploit. Regular updates and vigilant maintenance are essential to mitigate these risks, but many users neglect these practices, leaving their websites exposed to attacks.
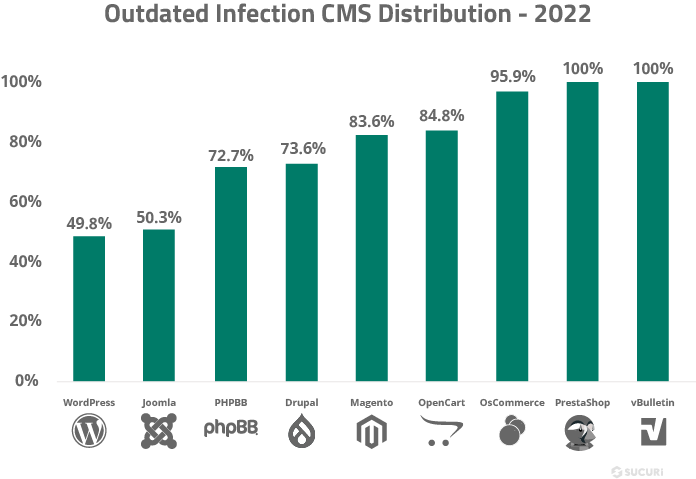
In summary, the combination of open access to the source code, the widespread use of these systems, and the reliance on third-party plugins and themes create a fertile ground for hackers. Ensuring robust security measures and staying vigilant with updates are crucial steps for website owners using open-source CMS platforms to protect against these threats.
13 Steps you can take to secure your website

Protecting your website not only safeguards your data and maintains your reputation but also builds trust with your audience. There are several crucial steps you can take to secure your website, including keeping software and security patches up-to-date, implementing SSL and HTTPS, and enforcing the use of complex passwords.
By following these website security best practices, you can fortify your website against common threats like data breaches, Denial of Service (DoS) attacks, ransomware, and more, ultimately providing a safer online experience for your users.
1. Keep software and security patches up-to-date
Regularly updating your website’s software and applying security patches is crucial for maintaining its security. Software vendors frequently release updates to fix vulnerabilities that could be exploited by attackers. By keeping your systems up-to-date, you close potential entry points for hackers and protect your site from known threats.
2. Add SSL and HTTPS
Implementing SSL (Secure Sockets Layer) and HTTPS (HyperText Transfer Protocol Secure) ensures that data transmitted between your website and its users is encrypted. This not only protects sensitive information like login credentials and personal details but also boosts your site’s trustworthiness and search engine rankings. HTTPS is essential for any website handling user data.
3. Require complex passwords and frequent changes
Enforcing the use of complex passwords and requiring regular password changes can significantly reduce the risk of unauthorized access. Complex passwords should include a mix of uppercase and lowercase letters, numbers, and special characters. Regularly updating passwords helps mitigate the risk of compromised credentials being used to breach your site.
4. Restrict administrative privileges
Limiting administrative privileges to only those who absolutely need them minimizes the risk of accidental or malicious changes to your website. Use role-based access control (RBAC) to assign appropriate permissions based on user roles, ensuring that critical operations are only performed by trusted personnel.
5. Change default settings
Changing default settings for your website’s software and applications can prevent attackers from exploiting known default configurations. Especially changing your default usernames, passwords, and other configurations which are often targeted by automated attacks, so customizing these settings adds an additional layer of security.
6. Backup your files
Regularly backing up your website’s files ensures that you can quickly recover from data loss or corruption caused by cyber attacks, hardware failures, or human error. Store backups in a secure, offsite location and test your recovery process to ensure you can restore your site effectively when needed.
7. Use a web application firewall (WAF)
A Web Application Firewall (WAF) protects your website by filtering and monitoring HTTP traffic between your site and the internet. It helps block malicious traffic and prevent attacks such as SQL injections, cross-site scripting (XSS), and other common threats. Implementing a WAF is a proactive step to safeguard your site from potential exploits.
8. Implement multi-factor authentication (MFA)
Multi-Factor Authentication (MFA) adds an extra layer of security by requiring users to provide two or more verification factors to access your site. This could include something they know (password), something they have (security token), or something they are (biometric verification). MFA reduces the risk of unauthorized access even if passwords are compromised.
10. Regularly monitor logs and conduct security audits
Monitoring your website’s logs and conducting regular security audits can help you detect suspicious activity and vulnerabilities early. By analyzing logs and reviewing your security measures periodically, you can identify potential threats and address them before they escalate into serious breaches.
11. Use a Content Delivery Network (CDN)
A Content Delivery Network (CDN) distributes your website’s content across multiple servers worldwide, enhancing its performance and security. CDNs can help mitigate Distributed Denial of Service (DDoS) attacks by absorbing traffic spikes and ensuring continuous availability. They also improve load times for users, providing a better overall experience.
12. Limit sensitive information collected and stored
Minimizing the amount of sensitive information your website collects and stores reduces the potential impact of a data breach. Only gather essential data and ensure it is securely stored and encrypted. Regularly review your data collection practices and remove any unnecessary information to limit your exposure to risk.
13. Educate and train employees on best practices
A crucial element of website security is ensuring that all employees are well-educated and trained on the latest security best practices. Cybersecurity isn’t solely the responsibility of IT departments; it requires a collective effort across the entire organization.
Regular training sessions can help employees recognize phishing attempts, understand the importance of strong password policies, and follow secure data handling procedures. By fostering a culture of security awareness, you can significantly reduce the risk of human error, which is often a critical vulnerability in the cybersecurity chain.
Encourage employees to stay updated on new threats and to report suspicious activities immediately, ensuring a proactive approach to maintaining robust website security.
Prepare a recovery plan before anything happens

When it comes to website security, having a robust recovery plan in place is essential for mitigating the effects of unforeseen cyber incidents. A well-prepared disaster recovery plan (DRP) ensures that your organization can swiftly restore its IT operations and data in the event of an attack, minimizing downtime and preserving business continuity.
A DRP typically includes policies, step-by-step procedures, and specific responsibilities assigned to team members to recover IT systems and data. Testing the plan regularly is crucial to ensure its effectiveness during an actual disaster. By having a DRP, your organization can reduce risk exposure, maintain economic stability, and potentially lower insurance premiums and liability. Not only does this safeguard your critical data and systems, but it also ensures compliance with regulatory requirements and can save your organization significant costs associated with system downtime and lost productivity.
In addition to standard backup and recovery processes, your DRP should address the removal of malware, restoration of infected files, and overall system recovery to a secure state. By integrating these elements into your recovery plan, you can ensure a comprehensive approach to maintaining your website’s integrity and functionality in the face of various cyber threats.
How we secure our clients’ websites
At Dytatek, protecting our clients’ website data is a top priority. We leverage cutting-edge security solutions from industry leaders like SUCURi to ensure comprehensive protection against a wide range of cyber threats. Here’s a detailed look at how we safeguard your digital assets:
- SSL and HTTPS Implementation:
- To encrypt data transmitted between your website and its users, we ensure the implementation of SSL certificates and enforce HTTPS protocols.
- This encryption prevents data interception and enhances user trust.
- Malware Scanning and Removal:
- Regular malware scans are conducted to identify and remove any malicious code that may have been injected into your website.
- Our team ensures that any detected threats are promptly neutralized, keeping your site clean and secure.
- Security Hardening:
- We apply stringent security measures to harden your website against attacks. This includes implementing secure coding practices, updating software, and configuring server settings to reduce vulnerabilities.
- Default settings are adjusted to close common security loopholes, making it harder for attackers to exploit weaknesses.
- Regular Security Audits:
- Periodic security audits are conducted to assess the effectiveness of our security measures and identify areas for improvement.
- These audits help us stay ahead of emerging threats and continuously refine our security strategies.
- Continuous Monitoring and Detection:
- We have available round-the-clock monitoring systems to detect potential threats and vulnerabilities in real-time.
- By constantly analyzing traffic and user behavior, we can quickly identify and respond to suspicious activities, minimizing the risk of breaches.
- Web Application Firewall (WAF):
- SUCURi’s advanced WAF filters out malicious traffic and blocks potential attacks before they reach your server.
- This additional layer of defense is available as an add-in to help protect against SQL injections, cross-site scripting (XSS), and other common web exploits.
- Backup Solutions:
- Comprehensive backup solutions are available to ensure that your data can be quickly restored in the event of an attack or data loss incident.
- Regular backups provide an additional layer of protection, enabling quick recovery and minimizing downtime.
At Dytatek, our proactive approach to website security ensures that your digital presence remains resilient against evolving cyber threats, allowing you to focus on growing your business with peace of mind.
By leveraging these comprehensive security measures, we aim to provide a safe and secure online environment for your business, ensuring that your website remains operational and your data protected.
Protect Your Website with Our Free Security Checklist!

As cybersecurity threats continue to evolve, staying informed and proactive is more crucial than ever. That’s why we’ve created the Website Security Checklist: Protect Your Website in 2024.
This eBook is packed with expert advice and actionable steps to protect your website from potential vulnerabilities, ensuring your online presence is secure. From data protection tips to a comprehensive security checklist, this guide will help safeguard your business.